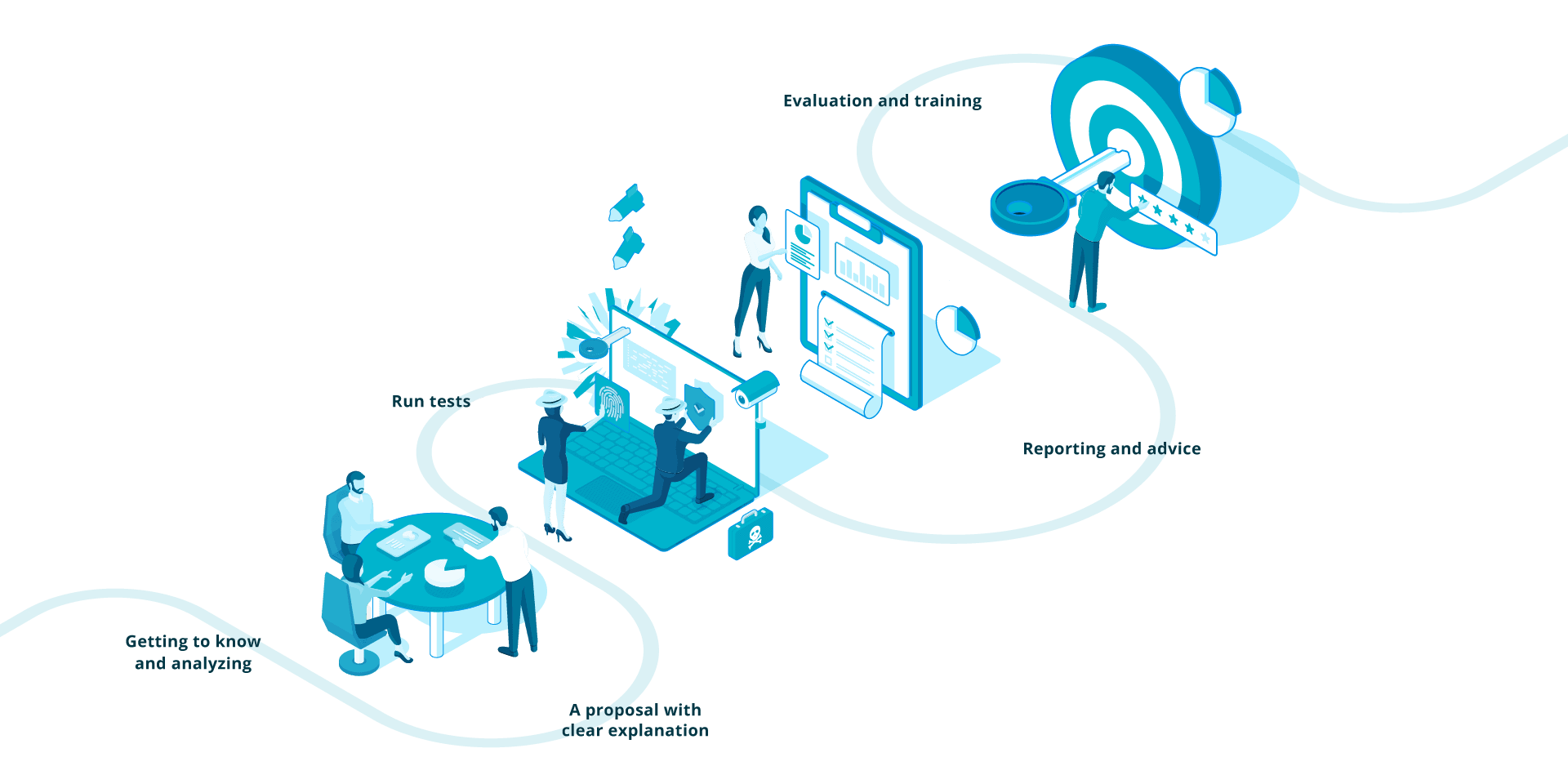
Have your website hacked, but ethically and without stress. Would you like an expert to think along at a strategic or policy level? Or train your employees? The S-Unit does it all. It is not without reason that we are your security companion.
Directly to
Our approach






Pentesting

External Attack Surface
Through a penetration test on the external attack surface, we investigate how an attacker can gain access to your network. Examples of techniques are conducting phishing campaigns, testing WiFi networks, physically placing drop devices in the network, collecting open source intelligence and performing vulnerability scans on your external infrastructure.

Internal networks
Penetration testing on internal networks provides insight into the next steps of an attacker with access to the network. This can concern regular office automation networks, but also extra secure networks, such as those used for Supervisory Control and Data Acquisition (SCADA) systems or other Industrial Control Systems (ICS).

Applications
Penetration tests on individual applications provide an in-depth insight on the security level of (customized) applications. We provide advice on vulnerabilities in custom code, unsafe use of development frameworks and unsafe configuration of applications and underlying infrastructure. Think of penetration tests on web applications, APIs, mobile applications and Mendix applications.
Hardware and images
Are you launching your own Internet-of-Things (IoT) device, are you about to roll out new images for your workplaces, or do you want to periodically test your point-of-sale systems? We help you implement this in a secure way.

Offensive as a Service
With Offensive as a Service (OaaS) we provide a program in which we periodically perform testing activities. Whether you want to have the same environment tested monthly, choose to have a broad surface tested over several quarters or want penetration tests to match sprints, we cater to your needs.

Unknown
A creative hacker sees potential opportunities for abuse everywhere. This makes it practically impossible to list all possible penetration tests. Do you have another issue that you would like a hacker to take a look at? We are happy to look at the possibilities together and what we can do for you.
Red teaming

Modular red teaming
Stel een red teaming project samen dat precies aansluit bij uw wensen en informatiebehoeften. Wij bieden red teaming diensten aan op basis van modules, waarbij een module één of meer activiteiten met een specifiek doel binnen het project bevat. We gaan graag met u in gesprek over uw informatiebehoeften om samen tot een passende samenstelling van modules te komen.

TIBER-NL
Het TIBER-NL programma, geleid door De Nederlandsche Bank, heeft als doel om de cyberweerbaarheid van de financiële sector te verhogen. Het raamwerk dat hieruit voortvloeit, is daarnaast ook goed bruikbaar voor andere vitale sectoren, zoals de zorg-, telecom- of energiesector. Is uw organisatie verplicht een TIBER-NL uit te voeren of wenst u gebruik te maken van dit raamwerk? The S-Unit is de Red Team Provider voor uw TIBER-NL-test.

Purple teaming workshop
A direct collaboration between our hackers (the red team) and your security team (the blue team) to improve your detection and response capabilities. Choose a purple teaming workshop as part of your red teaming or stand-alone technique to take your Security Operations Center (SOC) to the next level.
Consultancy

Begeleiding & Advies
Guidance and advice on, among other things, security strategy and audits.

Cybercrisis Simulation
A dry run: how does the organization deal with a cyber incident? One or more interactive sessions under the guidance of information security experts from The S-Unit.

Interim (C)ISO
Temporarily strengthen your team with an Information Security Officer from The S-Unit. Our expert guides and advises you in the field of security.

Mystery Guest
We test whether your organization is sufficiently secure and whether your employees are alert enough. For this we send a mystery guest to infiltrate the organization.

Phishing Campaign
We test whether your employees recognize phishing emails and how they deal with them. With this we give a boost to their awareness and resilience.

Trends, Nieuws & Inzicht
Keep up to date with current trends and receive alerts about relevant threats.

CLaaS Tool
With the CLaaS tool (Cryptolocker as a Service) designed by our specialists, we show you in a safe way what the consequences of a ransomware attack are for your organization.

Kraken Tool
With the Kraken tool designed by our specialists, you gain insight into the weak passwords among employees.
The S-University

Trainings
Onze kennis en kunde brengen we als onderdeel van onze missie over op vakgenoten via onze trainingen. Samen bouwen aan een veiligere digitale maatschappij.

CTF hacking event
During a Capture The Flag (CTF) hacking event of The S-Unit, teams compete against each other to solve as many challenges as possible within a certain time with the goal to learn to think like a hacker.

Lezingen & Presentaties
A lecture or presentation by the specialists of The S-Unit on security. They give tips and tricks to improve your security.

Online Education Platform
Our intuitive and accessible Security Awareness Platform makes the right training material available to the right people at the right time.

Workshop
The security experts of The S-Unit give a tailor-made security workshop within your organization full of tips and tricks, based on years of experience.

Webinars
In an online webinar we talk about a security related topic. If you have a suggestion for a topic, please let us know.


