Red Teaming
Ethical hacking
Wat is Red teaming?
Red Teaming, also known as adversary simulation, is an offensive method for testing cybersecurity. A realistic attack simulation tests an organization’s cyber resilience against a sophisticated attacker. Like other offensive methods, it uses the mindset of hackers to look at an organization’s security. The ethical hackers running the simulation are called the Red Team. The various teams responsible for security within the organization to test together are called the blue team. For alignment and coordination, a select number of involved individuals from within the organization are tested, and together, they form the white team.
Wat is het doel van een Red teaming?
A Red Teaming serves two primary purposes. First, it is a measurement of the organization’s current resilience level. How mature is the organization regarding cybersecurity, and does it match expectations? This is an important starting point for defining a broader security strategy. Secondly, Red Teaming is an opportunity for security teams to learn from their adversaries. Discover how sophisticated attackers try to stay under the radar and how detection and response capabilities can be improved to detect the use of such techniques anyway.
Waarom kiezen voor Red teaming?
Our approach goes beyond attack simulations. At The S-Unit, we provide an in-depth evaluation of your security measures and reveal valuable insights that protect your organization from advanced threats.
Wij passen een realistische aanvalssimulatie toe en ons doel is om te verifiëren of jouw totale set aan beveiligingsmaatregelen afdoende bescherming biedt tegen echte aanvallers. We gaan verder dan alleen het blootleggen van kwetsbaarheden door ook te testen of de detectie- en responsmaatregelen effectief zijn. Op onopvallende wijze dagen we jouw securityteam uit om een aanval in hun netwerk op te sporen. Met de afsluitende Gold Teaming tenslotte testen we ook of de procedures in geval van een cyberaanval effectief zijn.
At The S-Unit, we offer modular Red Teaming services so you can create the perfect combination of modules to suit your needs and requirements. We are the right choice if you are looking for a Red Teaming provider familiar with frameworks such as TIBER-NL, ART, or ZORRO. Our experienced hackers simulate advanced threat tactics with state-of-the-art capabilities. Make a wise choice and opt for Red Teaming at The S-Unit.

Modular red teaming
Using our modular Red Teamings, you can put together a Red Teaming project that exactly matches your needs and information requirements. We will be happy to discuss your needs with you to devise a suitable composition of modules.

Framework Red Teaming
Are you looking for a red teaming provider for a test using a framework like TIBER-NL, ART or ZORRO? Take advantage of The S-Unit's expertise and experience in simulating advanced threat actors with state-of-the-art capabilities.

Purple Teaming
A direct collaboration between our hackers and your security team to improve your detection and response capabilities. Choose a purple teaming workshop as part of your Red teaming or a standalone technique to take your security operations centre to the next level.
Team Collaboration in Red Teaming
Red Teaming is a crucial method for measuring an organisation's current resilience. Within this process, a colour code distinguishes different teams, each with a unique role and responsibility.
• Red team: this ethical hacking team performs realistic attacks to expose vulnerabilities and test security resilience.
• Blue team: the defensive team maintains security and discovers and stops attacks during the simulations.
• White team: are selected individuals responsible for coordinating and evaluating responses to the attack simulations.
• Purple team: A mix of red and blue, this team is focused on working together to discover vulnerabilities and improve security.
• Gold team: Also known as cyber crisis simulation, this team integrates the different colours into the Red Teaming process. Here, the specific colours indicate activities.
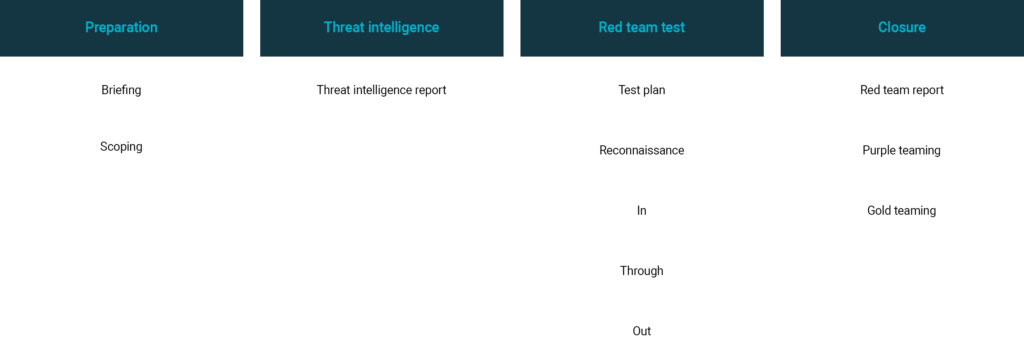
Red Teaming modules
The S-Unit offers Red Teaming services on a module basis. It allows red teaming to tailor to the client's needs and information requirements. The modules are divided into four phases. These phases and modules are based on the TIBER-NL and ART frameworks. The following modules are available for each phase:
Fase
Module
'Where a penetration test can be seen as a test, a Red Teaming is the final exam.'
Red Teaming: meer dan een cybersecurity test
Red Teaming is more than an offensive cybersecurity testing method; it is a mindset. A realistic attack simulation tests resilience and provides valuable insights and learning opportunities. In short, Red Teaming with The S-Unit delivers a comprehensive evaluation of cybersecurity and useful insights and learning opportunities for organizations striving to maximize protection against advanced cyber threats.
Red Teaming Updates