Have your website hacked, but ethically and without stress. Would you like an expert to think along at a strategic or policy level? Or train your employees? The S-Unit does it all. It is not without reason that we are your security companion.
Our approach
The S-Unit stands for customization. Because every organization has its own environment, challenges and needs. That is why we start a conversation to find out what best suits your organization. We use a fixed approach and thus come together to a solid plan. To stay one step ahead of attackers continuously.
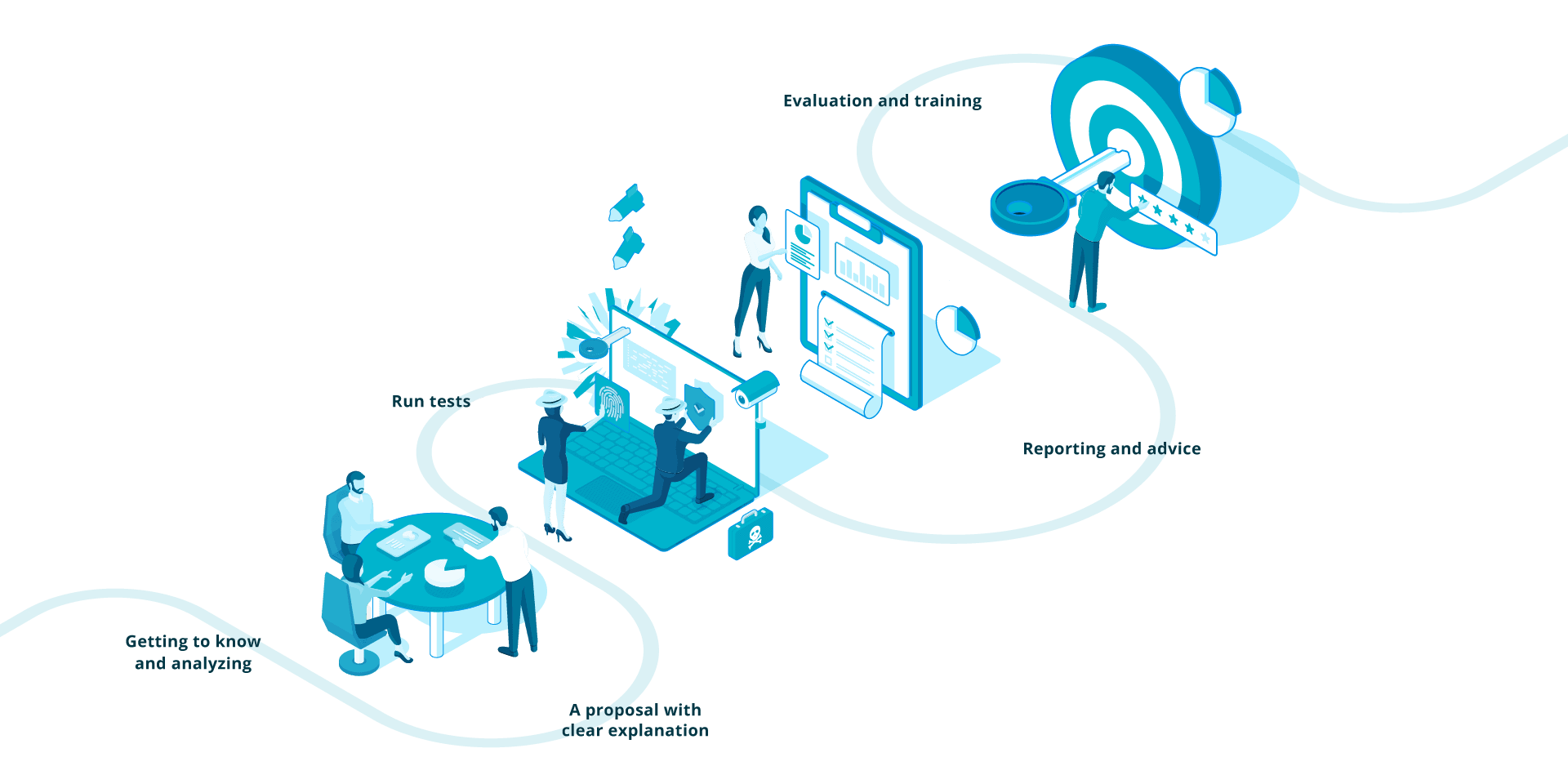
Getting to know and analyzing
To really get you started, we want to know who your organization is and what is important to you. That is why we take extensive time to get to know you. In one or two meetings we get an idea of the organization, IT, wishes and needs and we discuss how The S-Unit can provide added value. One of our hackers joins in order to ask the difficult technical questions. In this way, we can be sure that we take all aspects into consideration.
A proposal with clear explanation
After getting acquainted and scoping your security needs, we come up with a proposal in which we clearly explain how we implement our services. The needs, description of the scope and your specific research questions are the basis for our action plan. An action plan that exactly matches your organizational needs. From a test on one component to a structured approach for complete IT security. With consultancy and employee awareness where it is necessary.
Run tests
Our specialists, all hackers with a heart, test the security status of your systems. From an attacker's perspective, we map your IT and determine the attack vectors. We think creatively and out-of-the-box. It is the best way to discover vulnerabilities. Our priorities and focus are on the formulated research questions. Because that is where we add the most value for your organization. But, stubborn as we are, we look just a little further. Because we want to leave no stone unturned.
Reporting and advice
We report our results in a clear manner. Because we want everyone in your organization to understand how your company can be hit by an attack. And if you wish, we present the results and advice at every level within the organization. Our report provides sufficient information for both the technical reader and the CEO to get started.
Evaluation and training
Keeping up, improving ourselves and continuously adapting to developments. It's exactly how we play the game. That is why we evaluate after every case, so that we can help you even better the next time. And of course, we also like to look ahead. So we would also like to hear from you if there are additional points for attention or if you want to tackle another security issue.
We are in business. We don't hide behind a screen. With one leg in the community and the other in business, we understand the challenges of different markets and organizations.
Pentesting
Offensive security often starts with a penetration test. Because we understand that you want to know if and where your organization is vulnerable. Of course, we look at what is important to you. Your crown jewels. It is the mission of our hackers to gain insight into the security status of your IT. And then translate that into clear insights and concrete points for improvement.
Offensive Security. Do not wait and see, but proactively map out risks.

External Attack Surface
Through a penetration test on the external attack surface, we investigate how an attacker can gain access to your network. Examples of techniques are conducting phishing campaigns, testing WiFi networks, physically placing drop devices in the network, collecting open source intelligence and performing vulnerability scans on your external infrastructure.

Internal networks
Penetration testing on internal networks provides insight into the next steps of an attacker with access to the network. This can concern regular office automation networks, but also extra secure networks, such as those used for Supervisory Control and Data Acquisition (SCADA) systems or other Industrial Control Systems (ICS).

Applications
Penetration tests on individual applications provide an in-depth insight on the security level of (customized) applications. We provide advice on vulnerabilities in custom code, unsafe use of development frameworks and unsafe configuration of applications and underlying infrastructure. Think of penetration tests on web applications, APIs, mobile applications and Mendix applications.
Hardware and images
Are you launching your own Internet-of-Things (IoT) device, are you about to roll out new images for your workplaces, or do you want to periodically test your point-of-sale systems? We help you implement this in a secure way.
Offensive as a Service
With Offensive as a Service (OaaS) we provide a program in which we periodically perform testing activities. Whether you want to have the same environment tested monthly, choose to have a broad surface tested over several quarters or want penetration tests to match sprints, we cater to your needs.

Unknown
A creative hacker sees potential opportunities for abuse everywhere. This makes it practically impossible to list all possible penetration tests. Do you have another issue that you would like a hacker to take a look at? We are happy to look at the possibilities together and what we can do for you.
Red teaming
The core of offensive security lies in seeing security through the eyes of a hacker. You cannot get closer to this than with a red teaming. We use a realistic attack simulation to measure the resilience of your organization against an advanced attacker. Where a penetration test can be seen as a test, a red teaming is the final exam.
Offensive Security. Do not wait and see, but proactively map out risks.

Modular red teaming
Put together a red teaming project that exactly matches your wishes and information needs. We offer red teaming services based on modules, where a module contains one or more activities with a specific goal within the project. We would be happy to discuss your information needs with you in order to come to a suitable composition of modules together.

TIBER-NL
The TIBER-NL programme, led by the Dutch Central Bank, aims to increase the cyber resilience of the financial sector. The resulting framework is also very useful for other vital sectors, such as the healthcare, telecom or energy sector. Is your organization obliged to carry out a TIBER-NL or do you wish to use this framework? The S-Unit is the Red Team Provider for your TIBER-NL test.

Purple teaming workshop
A direct collaboration between our hackers (the red team) and your security team (the blue team) to improve your detection and response capabilities. Choose a purple teaming workshop as part of your red teaming or stand-alone technique to take your Security Operations Center (SOC) to the next level.
Consultancy
Offensive security is also about making the organization better equipped to make it resilient against attacks. A complex issue that is often comprehensive. The S-Unit then fulfills the role of sparring partner. Our consultants help bring your organization's security level to the desired level.
Security consultancy. Mapping out the problems. In plain language. To give clear advice.

Guidance & Advice
Guidance and advice on, among other things, security strategy and audits.

Cybercrisis Simulation
A dry run: how does the organization deal with a cyber incident? One or more interactive sessions under the guidance of information security experts from The S-Unit.

Interim (C)ISO
Temporarily strengthen your team with an Information Security Officer from The S-Unit. Our expert guides and advises you in the field of security.

Mystery Guest
We test whether your organization is sufficiently secure and whether your employees are alert enough. For this we send a mystery guest to infiltrate the organization.

Phishing Campaign
We test whether your employees recognize phishing emails and how they deal with them. With this we give a boost to their awareness and resilience.

Trends, News & Insight
Keep up to date with current trends and receive alerts about relevant threats.

CLaaS Tool
With the CLaaS tool (Cryptolocker as a Service) designed by our specialists, we show you in a safe way what the consequences of a ransomware attack are for your organization.

Kraken Tool
With the Kraken tool designed by our specialists, you gain insight into the weak passwords among employees.
The S-University
How do you recognize phishing? What is a secure password? To keep your organization safe, your employees must have sufficient knowledge and skills. The S-University trains them on that. In doing so, we pay attention to all essential aspects.
Security university. Working security aware through training and education.

Trainings
As part of our mission, we transfer our knowledge and expertise to colleagues through our trainings. Building a safer digital society together. See our trainings here.
Capture the Flag hacking event
During a Capture The Flag (CTF) hacking event of The S-Unit, teams compete against each other to solve as many challenges as possible within a certain time with the goal to learn to think like a hacker.
Lectures & Presentations
A lecture or presentation by the specialists of The S-Unit on security. They give tips and tricks to improve your security.

Online Education Platform
Our intuitive and accessible Security Awareness Platform makes the right training material available to the right people at the right time.

Workshops
The security experts of The S-Unit give a tailor-made security workshop within your organization full of tips and tricks, based on years of experience.

Webinars
In an online webinar we talk about a security related topic. If you have a suggestion for a topic, please let us know.

Would you like to know more about the services of The S-Unit? Or do you have another S-ential question for us?










