How does Red Teaming work?
The S-Unit offers red teaming services based on modules. This makes it possible to tailor red teaming to the wishes and information needs of our customers. The modules are based on the TIBER-NL framework and are divided into four phases. The diagram below shows the available modules per phase.
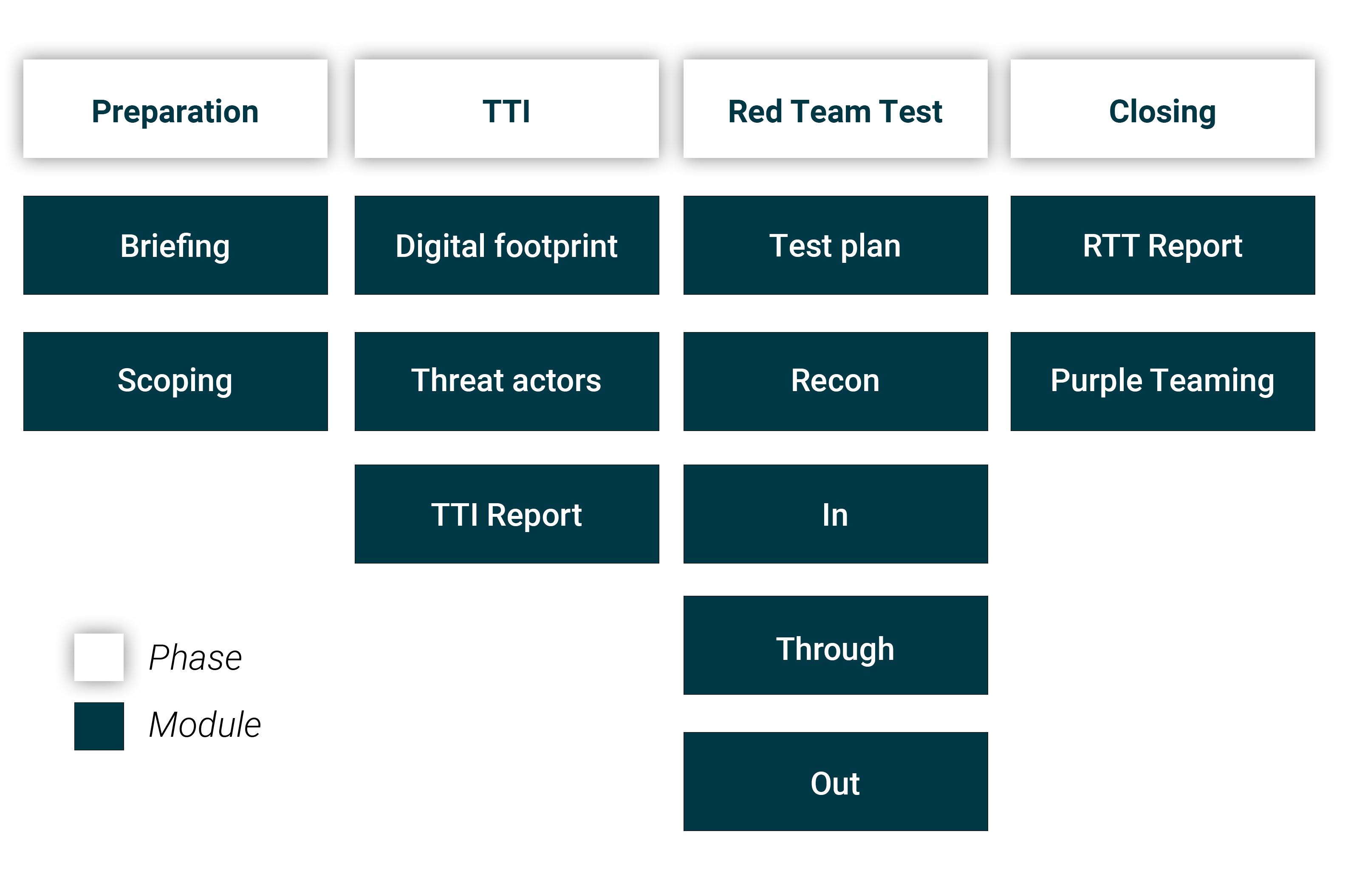
1. Preparation phase
1.1 Briefing
During the briefing, various operational aspects of the project are coordinated with the client. In any case, it concerns the following matters:
- Getting acquainted between involved team members of the client and The S-Unit;
- Alignment of a project schedule, consisting of:
- Checkpoints for the different modules;
- Interim meetings to discuss the progress of the project;
- Making operational agreements regarding communication and escalation paths;
- Verification of the disclaimer;
- Discuss outstanding action points.
1.2 Scoping
In the scoping, possible goals for attack scenarios with a major impact within and outside an organization are defined. This is done in three steps:
- Determining the critical functions
- Determining the critical systems
- Determining the possible flags
Critical functions are the people, processes and technologies that are critical to the delivery of a core service of an organization and where the disruption of the function results in:
- Impact on the stability of the organization;
- Impact on the position of the organization in the market;
- Impact on the organization's customers;
- Social impact.
Critical systems are the IT systems underlying the critical functions. The S-Unit will attempt to demonstrate that it is possible to compromise critical functions by abusing the underlying critical systems. A pre-agreed action is carried out. This is called capturing the flag. Depending on the agreed action, dummy data can be used as a flag. This may be desirable when the flag involves highly sensitive information.
2. Targeted threat intelligence phase
2.1 Digital footprint
This module is used to determine which attack techniques can potentially be used against an organization. For example: accessing the internal network via a virtual desktop is only possible if the organization in question actually uses virtual desktops. To be able to draw up a scenario, the digital footprint of the organization is mapped using public and closed sources on the internet and the deep web. The digital footprint refers to all information that is disclosed digitally, which can be relevant for an attacker to penetrate the organization. Think of domain names, IP addresses and email addresses, but also information relevant to physical intrusion, such as information regarding building entrances, type of security gates and appearance of access passes. This may concern information that the organization discloses itself, but also information that is shared by employees and third parties.
2.2 Threat actors
Within this module, information is collected that can be used to sort potential attack techniques by relevance. This is done by mapping threat actors that may target an organization and their modus operandi. For the selection of relevant threat actors, Advanced Persistent Threats (APTs) are considered. An APT is an attack group that has performed multiple attacks against different organizations with a high degree of technical complexity. By looking at different characteristics of historical targets of an APT, groups can be identified that might target an organization. For each of these relevant APTs, the modus operandi, also known as tactics, techniques and procedures (TTPs), investigated. This gives an idea of the capabilities of possible opponents of the organization. This image can then be used to determine which TTPs are most relevant to test during red teaming.
2.3 TTI report
If you wish to use the digital footprint and/or the threat actors module, we will communicate our interim findings in the TTI reporting module. The TTI report Module concerns an interim report with the results of the scoping module and the TTI phase. This report contains the following elements:
- Management summary;
- Business overview;
- Critical functions and systems;
- Digital footprint;
- Threat actors;
- Example attack scenarios.
3. Red Team test phase
3.1 Test plan
The test plan broadly describes the attack scenario that will be executed. A test plan contains the following elements:
- The end goal of the scenario;
- The critical system that will be abused to achieve this goal;
- The threat actor being simulated;
- The TTPs that will be used;
- Checkpoints and deadlines for parts of the screenplay;
- Possible leg-ups for the different modules;
The TTPs that are recorded in the test plan form a guideline. It is impossible to determine in advance exactly which techniques are required to achieve the goal and whether each technique is applicable to the organisation's environment. If the TTPs from the test plan are insufficient to achieve the target, additional TTPs will be used. If a TTP does not apply to the environment, a replacement can be used.
3.2 Reconnaissance
Reconnaissance concerns the collection of the necessary information for the penetration of the organization by means of the techniques defined in the test plan. The information required depends on the chosen technique for obtaining initial access. To illustrate, we compare two techniques: sending a phishing document and placing a drop device. The table below shows examples of information that may be relevant for both techniques.
Phishing document | Drop device |
|
|
Information gathering in this module can take place, among other things, by:
- Consulting public and closed sources on the internet and deep web;
- Performing active scans on the infrastructure of an organization;
- Performing active scans on the infrastructure of an organization;
- Physically visiting (office) locations of the organization.
Compared to the Digital footprint module, this module searches for much more specific information with a larger arsenal of techniques. The latter also means that the information gathering in this phase of the project can be detected by the blue team.
3.3 In
The In involves preparing and executing an attack to gain initial access to the organization. Both the preparation and implementation are highly dependent on the defined scenario. To illustrate, we compare the same two techniques as in the Reconnaissance module: sending a phishing document and placing a drop device.
Phishing document | Drop device | |
Preparation |
|
|
Execution |
|
|
3.4 Through
The Through module concerns the phase between the moment when initial access is obtained and the moment when the end goal of the scenario can be executed. In this phase, work is done on:
- Maintaining access to the environment by:
- Preventing of detection;
- Compromising additional systems to gain a stronger position in the network;
- Increasing environmental rights;
- Gather information required to capture the flag.
Because preventing detection plays an important role, automated scans are not used. In addition, the client does not share any technical information with regard to the IT environment. For example, the red team does not know:
- Where the critical systems are located in the network.
- Which network paths provide access to critical systems.
- How authentication for critical systems is set up.
To gain access to critical systems, the red team itself collects the necessary technical information through the access it has gained to the environment. Depending on the flag, process information may also be required. For example, if the flag is defined as “executing a rogue payment of €5.00 through application X”, then gaining access to application X is often insufficient to actually make a rogue payment. This requires an understanding of the payment process and the role system X plays in this process. Only when it is clear how payments are imported, who approves them and what additional checks will take place, can a payment actually be made. These factors make the Through module, although similar to a penetration test, is a lot more time consuming.
3.5 Out
With the Out module, the impact of the attack is demonstrated by capturing the flag. When a flag is captured by the red team, the scenario is completed. A scenario can also be completed when the planned time has elapsed or when the client requests that the scenario be stopped prematurely.
4. Closing phase
4.1 Red Team test report
After completion of the red team test phase, a report with results will be delivered with detailed information about the implementation, outcomes and advice.
4.2 Purple Teaming
During a Purple teaming workshop The S-Unit works together with the blue team of the client to improve the detection and response capabilities of an organization. The blue team are all individuals responsible for detection and response for an organization. This can, for example, concern an internal security operations center (SOC) but also SOC services that are purchased from a third party. During an interactive session, The S-Unit repeats various actions from the performed scenarios to generate input for the blue team's tooling. Then both teams work together to create new views and detection rules. In addition, The S-Unit can provide detailed advice and action points for further improvement after the workshop. The exact content of a purple teaming workshop depends on the wishes of the organization, but also on the available tooling and the configuration of this tooling.




